Introduction
The financial sector is facing a level of cyber risk that continues to intensify year after year. According to IBM’s 2024 Global Data Breach Report, the average cost of a breach in the Middle East reached USD 4.88 million, one of the highest globally. Even more concerning, 61% of global breaches start with compromised credentials, and attackers typically remain undetected for an average of 204 days before containment begins.
Financial institutions in Saudi Arabia already prime targets for sophisticated cyber adversaries must comply with the SAMA Cybersecurity Framework (CSF), one of the region’s most mature regulatory requirements. As digital banking expands, remote operations grow, and identity-based attacks surge, the only sustainable model is Zero Trust.
Secureify Trust, a fully self-hosted Zero Trust access platform, provides the identity assurance, access governance, and monitoring capabilities needed to meet SAMA CSF expectations with precision while keeping all data and audit trails fully sovereign inside KSA and even inside the financial institution's data center itself.
Understanding the SAMA Cybersecurity Framework (CSF)
SAMA CSF was designed to unify and raise the cybersecurity posture of Saudi Arabia’s financial institutions, ensuring that banks, fintechs, payment entities, and insurance companies are resilient against modern threats. It outlines a structured set of requirements across domains including:
Cybersecurity Governance
Cybersecurity Risk Management
Operational Controls
Third-Party Cybersecurity
Resilience
What SAMA makes very clear is that traditional perimeter-based security is no longer enough. The framework expects institutions to adopt identity-centric, data-centric, and context-aware security controls fundamental building blocks of Zero Trust.
For access security, network architecture, secure remote connectivity, and monitoring, the most relevant section is:
3.3 Operation & Technology
This section includes controls related to:
Access provisioning and least privilege
Privileged access management
Authentication and authorization
Network segmentation and secure connectivity
Logging, monitoring, and event analysis
Protection of logs and evidence
Continuous security event monitoring
Architecture-level security
These operational controls are where Zero Trust architecture delivers the highest compliance impact.
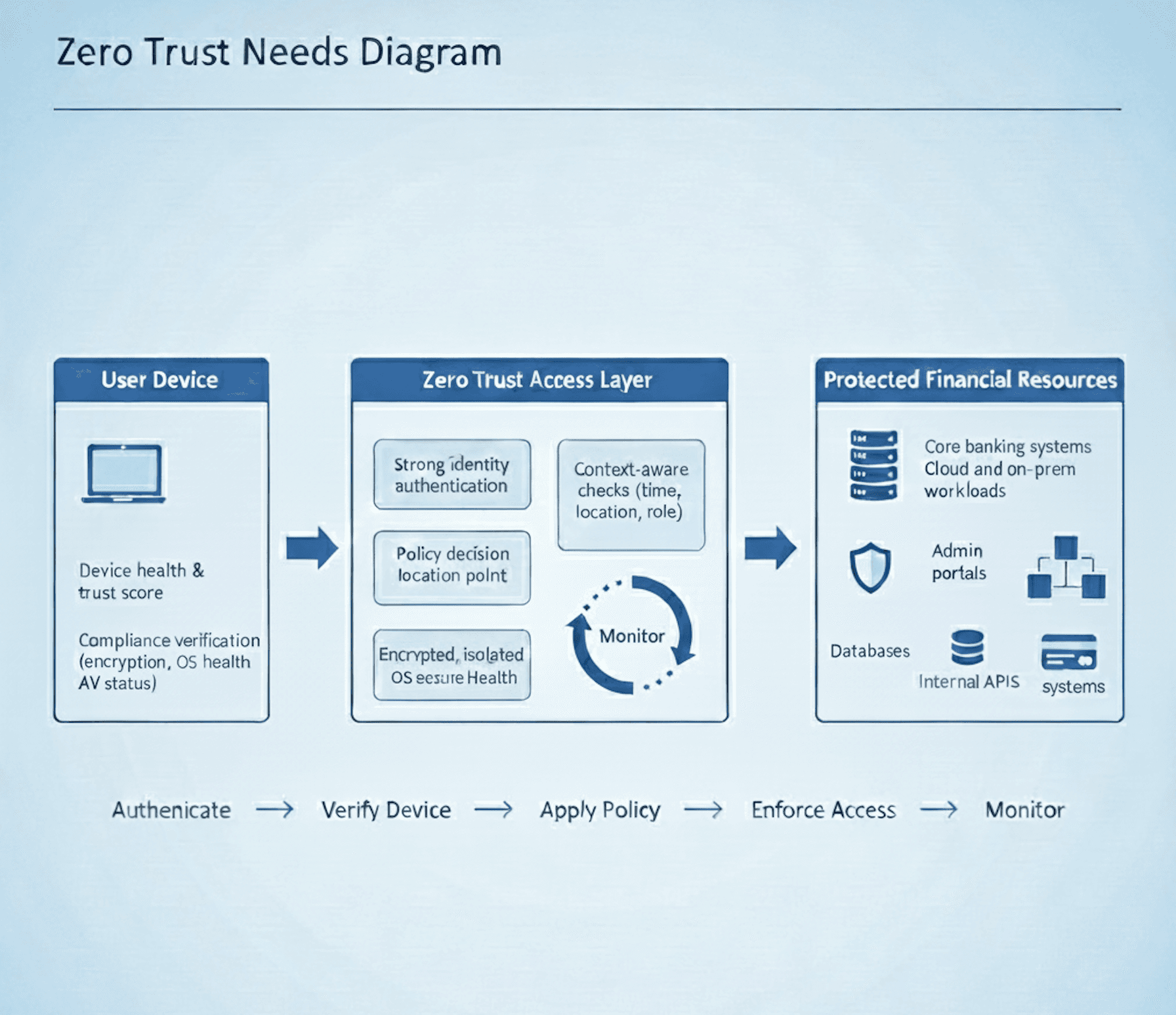
Enterprise grade Zero Trust Needs Diagram
This diagram shows how Secureify Trust enforces Zero Trust access: every request is authenticated, every device is verified, and every session is isolated and monitored before reaching financial systems—exactly as required by SAMA CSF.
How Secureify Trust Aligns With SAMA CSF Requirements
3.3 Operation and Technology — SAMA CSF Controls
Filtered specifically for: access, authentication, authorization, network protection, monitoring, logging, architecture, remote access, privilege management.
Secureify Trust → SAMA CSF Alignment Table
SAMA CSF Control ID | Control Description | How Secureify Trust Supports Compliance |
|---|---|---|
3.3.4-1 | Member Organization should establish and enforce strong access control practices | Secureify Trust enforces Zero Trust access through identity verification, device compliance checks, session limits, and policy-based authorization ensuring only verified users and compliant devices access financial system |
3.3.4-2 | Access control practices should ensure least privilege, segregation of duties | Every access request is evaluated per-resource and per-session. Secureify Trust eliminates over-privileged access by giving users access only to specific applications not the network |
3.3.4-3.a | Authentication mechanisms should be commensurate with criticality | Secureify Trust applies strong authentication with context validation, MFA enforcement, device posture verification, and continuous authentication throughout the session |
3.3.4-3.b | Authorization mechanisms must be risk-based | Access decisions are driven by policies incorporating risk signals such as device health, user role, time, location, and trust levels satisfying risk-based authorization |
3.3.4-3.e | Privileged access should be strictly controlled and monitored | Secureify Trust isolates privileged access pathways, enforces short-lived connections, and logs every administrative session with full traceability. Secureify Trust provides an API to integrate with any SIEM Solution |
3.3.5-1 / 3.3.5-2 / 3.3.5-3 / 3.3.5-4.a–e | Information system activity should be logged. Security events must be monitored. Logs should be protected against unauthorized access Logging completeness, synchronization, retention, and integrity requirements | Secureify Trust logs all user authentications, session activity, device validation results, and access decisions meeting full logging expectations also it provides an API to integrate with any SIEM Solution. Real-time monitoring of access behavior and anomalies helps institutions satisfy SAMA’s continuous monitoring expectations Logs remain fully self-hosted inside the institution’s infrastructure. No telemetry or logs leave the organization, satisfying log confidentiality Secureify Trust provides timestamped, consistent, tamper-resistant audit logs, exportable to SIEMs while remaining fully sovereign |
3.3.6-1 / 3.3.6-2 | Network security architecture must be designed and enforced | Zero Trust network access reduces attack surface by eliminating flat networks and enforcing isolated, application-level connections |
3.3.6-3.d–h | Controls on firewalls, IPS/IDS, segmentation, secure channels, DDoS protection | Secureify Trust supports segmentation by replacing VPN access with identity-based, encrypted tunnels that prevent lateral movement and reduce network exposure |
3.3.9-1 / 3.3.9-2 | Secure remote access must be enforced | Secureify Trust replaces traditional VPN with controlled per-resource access, ensuring remote users only reach what is approved satisfying SAMA’s secure remote access requirements |
3.3.10-1 / 3.3.10-2 / 3.3.10-3 | Security event monitoring must be centralized, automated, and continuous… | Secureify Trust’s access logs integrate directly with SIEM platforms, enabling centralized monitoring, anomaly detection, and compliance reporting |
3.3.11-f / 3.3.11-g | Incident handling and evidence protection… | Full traceability of access actions supports incident response, investigation, and forensic evidence requirements |
Maintaining Data Privacy & Sovereignty Under SAMA Expectations
Unlike cloud-hosted Zero Trust solutions, Secureify Trust operates fully self-hosted, giving financial institutions complete control over:
Cryptography and Sensitive Data
Network Traffic
Audit logs
Access analytics
Device context
Session metadata
No data leaves the organization, aligning with:
SAMA CSF confidentiality & sovereignty principles
Saudi PDPL
NCA CCC & ECC requirements
This is essential in the Kingdom, where regulators require full visibility and local control over sensitive financial access information.



