Organizations across the Middle East are facing an increasingly severe cyber threat landscape. According to IBM’s 2024 Global Data Breach Report, the average cost of a data breach in the Middle East reached USD 4.88 million, placing the region among the most impacted globally. Even more concerning, 61% of global breaches begin with compromised credentials, while attackers remain undetected for an average of 204 days providing ample opportunity for lateral movement and data compromise.
In the UAE, where digital government services, smart infrastructure, cloud adoption, and remote access are accelerating rapidly, these risks are amplified. To address them, the UAE Cybersecurity Council established the Information Assurance Regulation (IAR) as the national baseline for cybersecurity across government entities, critical national infrastructure, and regulated private-sector organizations.
Secureify Trust, a fully self-hosted Zero Trust access platform, enables organizations to meet IAR expectations through strong identity assurance, controlled access, continuous verification, and full data sovereignty while keeping all security telemetry and audit trails entirely within the UAE.
Understanding the UAE Information Assurance Regulation (IAR)
The UAE Information Assurance Regulation (IAR) initially introduced by NESA and now governed under the UAE Cybersecurity Council defines mandatory cybersecurity requirements for entities that support or operate critical digital services in the country.
IAR applies to:
Federal and local government entities
Semi-government organizations
Critical infrastructure sectors (energy, utilities, transportation)
Telecom operators
Healthcare institutions
Regulated private organizations supporting government services
The regulation establishes controls across key domains, including:
Identity and access control
Secure architecture and network protection
Operations security
Logging and monitoring
Incident response and resilience
Cloud and third-party security
Data confidentiality and sovereignty
At its core, IAR mandates that access to systems and data must be explicitly controlled, continuously monitored, and protected against both internal and external threats.
Why Zero Trust Is Essential for IAR Compliance
Cyber incidents in the region clearly demonstrate that traditional perimeter-based security models are no longer sufficient. Attackers increasingly exploit identity, credentials, and remote access rather than infrastructure vulnerabilities.
Key realities driving Zero Trust adoption in the UAE include:
Credential compromise as the leading attack vector globally
Rising insider threats and misuse of legitimate access
Increased remote and cloud-based operations
Higher breach impact where privileged access is involved
IAR expectations align naturally with Zero Trust principles, which require:
No implicit trust based on network location
Continuous authentication and authorization
Least-privilege access enforcement
Segmentation to prevent lateral movement
Full visibility into access activity
Secureify Trust enforces this model by design.
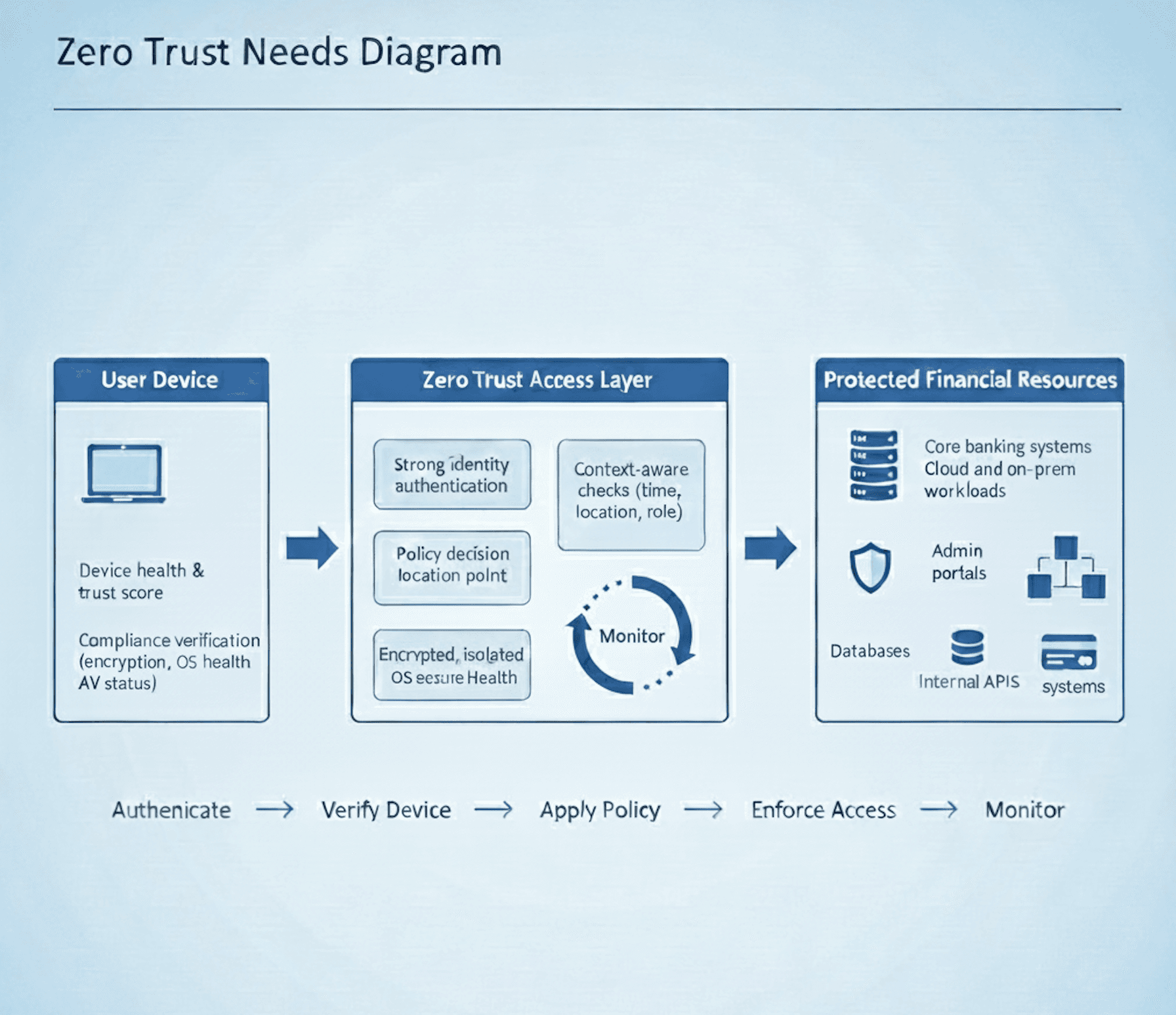
Zero Trust Needs
This diagram illustrates how Secureify Trust applies Zero Trust principles by validating identity, device posture, contextual risk, and access policy before allowing any connection to protected systems. Access is isolated, encrypted, continuously monitored, and limited strictly to approved resources directly supporting IAR requirements for secure access, network segmentation, and operational visibility.
How Secureify Trust Aligns With UAE IAR Requirements
Secureify Trust supports key IAR control domains related to access security, architecture, monitoring, and data protection by enforcing identity-centric access and continuous verification.
Access Control & Identity Assurance
IAR requires strong authentication, controlled access, and least-privilege enforcement. Secureify Trust ensures that every access request is authenticated, authorized, and constrained by policy, with access granted only to specific systems rather than entire networks.
Secure Architecture & Network Protection
IAR mandates secure system architecture and protection against lateral movement. Secureify Trust enables application-level access isolation, replacing broad network access models with tightly scoped, identity-based connectivity.
Logging, Monitoring & Incident Readiness
IAR emphasizes continuous monitoring and forensic readiness. Secureify Trust maintains comprehensive audit trails for access attempts, session activity, and policy decisions, enabling integration with SOC and SIEM platforms for real-time monitoring and incident response.
Endpoint & Device Trust
IAR requires that only trusted and secure endpoints connect to critical systems. Secureify Trust evaluates device posture before granting access, reducing the risk of compromised or unmanaged endpoints accessing sensitive environments.
Data Protection & Sovereignty
Data confidentiality and sovereignty are central to IAR. Secureify Trust is fully self-hosted, ensuring that identities, access logs, and security telemetry remain entirely within the organization’s infrastructure and within UAE jurisdiction.
A. Access Control (T5 Family)
Control ID | Control Name | Description | How Secureify Trust Aligns |
|---|---|---|---|
T5.1.1 | Access Control Policy | Establish and maintain an access control policy covering users, devices, privileged access, mobile access, and periodic review | Secureify Trust enforces centralized, policy-driven Zero Trust access. Access decisions are based on identity, device posture, and context, supporting formal access control policies and continuous enforcement |
T5.2 | User Access Management | Formal user registration, de-registration, and immediate revocation on role change or termination | Access is identity-bound and session-based. When a user is disabled or removed, access is instantly denied without reliance on static network permissions |
T5.2.2 | Privilege Management | Restrict, monitor, log, and audit all privileged access; require MFA | Secureify Trust enforces least-privilege access, time-bound sessions, strong authentication, and full audit logging for all privileged access paths |
T5.2.3 | User Security Credentials Management | Secure credential issuance, revocation, protection, and MFA for critical resources | Secureify Trust minimizes long-lived credentials by replacing them with policy-controlled, identity-verified access sessions protected by strong authentication. There is no also any credentials exposed to the end users. |
T5.4.4 | Remote Diagnostic & Configuration Protection | Restrict, authenticate, and log all remote diagnostic access | All remote access via Secureify Trust is encrypted, identity-verified, policy-approved, and fully logged |
T5.4.5 | Network Connection Control | Restrict network access based on predefined rules (role, time, purpose) | Secureify Trust removes broad network access entirely and allows access only to explicitly authorized systems and applications |
T5.4.6 | Network Routing Control | Prevent routing paths that violate access control policy; restrict lateral movement | Secureify Trust enforces application-level isolation, preventing lateral movement even after successful authentication |
T5.5 | Operating System Access Control | Prevent unauthorized OS access; monitor and log privileged usage | Secureify Trust restricts OS access to controlled, audited sessions rather than persistent administrative credentials |
T5.6.1 | Information Access Restriction | Restrict access to applications and information based on roles and responsibilities | Secureify Trust grants access only to the specific approved application or system, enforcing strict role-based access |
B. Logging, Monitoring & Auditability (T3 Family )
Control ID | Control Name | Summary | How Secureify Trust Aligns |
|---|---|---|---|
T3.6.1 | Monitoring Policy and Procedures | The entity shall establish a monitoring policy and procedures defining what is monitored, responsibilities, how often monitoring occurs, and how monitoring feeds incident response | Secureify Trust supports continuous access monitoring and provides structured security telemetry that can be integrated into the organization’s incident response and SOC processes through its Audit API |
T3.6.2 | Audit Logging | The entity shall produce and keep audit logs recording user activities, exceptions, and information security events; define activities captured, review frequency, retention, and ensure logs are reviewed by trained personnel | Secureify Trust generates detailed access audit trails (auth attempts, authorization decisions, session actions) that are SIEM-ready and support required review/retention practices |
T3.6.3 | Monitoring System Use | The entity shall monitor the use of information systems, define what is monitored, review frequency, retention, and ensure review by trained personnel | Secureify Trust continuously records and surfaces access/session behaviors, enabling monitoring of system use aligned to the organization’s monitoring program and SOC workflows |
T3.6.4 | Protection of Log Information | The entity shall protect log information against tampering and unauthorized access | Secureify Trust keeps access telemetry and logs in the customer-controlled environment and supports protections against unauthorized modification and access |
T3.6.5 | Administrator and Operator Logs | The entity shall log administrator and operator activities (what to capture, review frequency, retention) and ensure review by trained personnel | Secureify Trust enforces privileged session traceability and logging, enabling audits and investigations for administrative access paths |
C. Network Security & Segmentation (T4 Family)
Control ID | Control Name | Summary | How Secureify Trust Aligns |
|---|---|---|---|
T4.5.2 | Security of Network Services | The entity shall identify, define, and enforce security requirements for all network services to ensure that access to systems and information is restricted and protected in accordance with the access control policy | Secureify Trust enforces identity-based, encrypted access to services, reducing exposure of network services and ensuring access is granted only to authorized users and devices |
T4.5.3 | Segregation in Networks | The entity shall segregate networks, systems, and users based on risk, sensitivity, and business requirements to reduce the impact of security incidents and prevent lateral movement | Secureify Trust replaces flat network access with application-level Zero Trust access, ensuring users can only reach explicitly authorized systems and cannot move laterally |
D. Data Sovereignty & Information Protection
Control ID | Control Name | Summary | How Secureify Trust Aligns |
|---|---|---|---|
M5.2.4 | Data Protection and Privacy | The entity shall protect sensitive and personal information in accordance with applicable legal, regulatory, and privacy requirements, ensuring confidentiality, integrity, and controlled handling of information | Secureify Trust is fully self-hosted, ensuring all identity data, access metadata, and security telemetry remain under the organization’s control and within UAE jurisdiction |
Maintaining Data Privacy & Sovereignty Under UAE IAR Expectations
Unlike cloud-hosted Zero Trust solutions, Secureify Trust operates as a fully self-hosted platform, giving UAE government entities, critical infrastructure operators, and regulated organizations complete control over:
Cryptographic material and sensitive information
Network traffic and access pathways
Audit logs and security records
Access and session analytics
Device context and posture data
Session metadata and authorization decisions
No identity, access, or security telemetry leaves the organization’s environment. This directly aligns with:
UAE Information Assurance Regulation (IAR) confidentiality and sovereignty requirements
UAE Personal Data Protection Law (PDPL)
UAE Cybersecurity Council and former NESA directives
This level of control is essential in the UAE, where regulators require full visibility, accountability, and jurisdictional control over sensitive systems, access data, and national digital infrastructure.



